Keeping your money safe is our top priority.
or encounter any of these scams.

|
In the past few days we have seen an increase in fraudulent text messages claiming to be from the INSTITUTION FOR SAVINGS. The text asks the recipient to click on a link if they don't recognize a large debit from CVS, Costco and/or other retailers. THIS LINK IS FRAUDULENT! If you did click on the link, please call Deposit Services immediately at 978-462-3106.
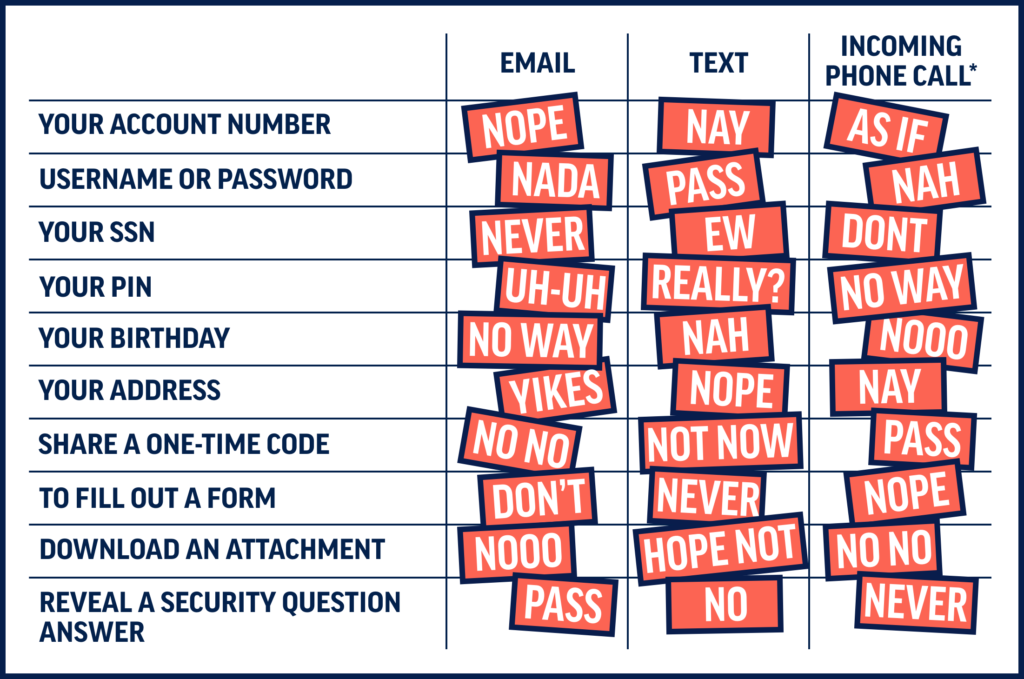
As always, we urge you to never give out your account information or security credentials, even if you think you know who is asking for it. Banks will never call and ask you to provide personal information over the telephone. (If you call us, you may be asked to provide information, however, to verify your identity.) We encourage you to review your account(s) regularly for any suspicious or unauthorized charges. If you have online banking, it is easy to do! If you do not use online banking, please contact us to set it up. We want to ensure that you are doing everything you can to protect your funds and personal information. Please call Deposit Services at 978-462-3106 if you have any questions or encounter any of these scams. |
We are proud to be one of only 193 banks, credit unions and financial advisory firms nationwide to have earned AARP's 2025 BankSafe Trained Seal in recognition of the steps we have taken to curb financial exploitation of older adults. A list of the financial organizations that received the 2025 BankSafe Trained Seal can be found here.
 Based on a Virginia Tech study, it is estimated that BankSafe-trained employees save customers 16 times more than frontline workers who don’t complete the training. Saving a record $137 million in 2024 – a 53% increase in dollars saved over the previous year – BankSafe has totaled more than $428 million in savings since its inception.
Based on a Virginia Tech study, it is estimated that BankSafe-trained employees save customers 16 times more than frontline workers who don’t complete the training. Saving a record $137 million in 2024 – a 53% increase in dollars saved over the previous year – BankSafe has totaled more than $428 million in savings since its inception.
To earn the esteemed seal, organizations must ensure at least 80% of their frontline staff complete AARP's comprehensive BankSafe training annually, alongside actively pursuing policies to address suspected financial exploitation. Eligibility for the seal also requires a positive standing in Better Business Bureau ratings and adherence to specific legal and regulatory standards.
Gift Card and Bitcoin ATM Scams Targeting Seniors Are on the Rise!
 We have seen a substantial increase in the number of customers who have been victims of scams utilizing gift cards and Bitcoin ATMs.
We have seen a substantial increase in the number of customers who have been victims of scams utilizing gift cards and Bitcoin ATMs.
The gift card scams start with a call, text, email, or social media message demanding immediate payment for a variety of reasons: money is owed the government, they are from tech support and will fix a computer issue, the customer has won money, a family member, often a grandchild, or a new “friend” is in trouble, etc. Scammers instruct the customer to purchase gift cards and then provide the redemption numbers on the cards to the scammer. Obviously the cards are then redeemed by the scammer and the customer loses those funds used to purchase the cards.
Another scam that is prevalent recently is related to the use of bitcoin ATMs. Scammers call, impersonating government, law enforcement, utility or other officials and ask for money. Using fear and intimidation tactics, they then direct customers to withdraw money from their banks, investment, or retirement accounts, then direct them to Bitcoin ATMs. They then direct the customers to deposit their funds into the ATMs, sending the money to the scammers using QR codes they provide. The funds are then gone and untraceable in most instances.
Please be aware of these sophisticated scams targeting seniors and to avoid falling for them no matter how convincing the scammers can be. Our employees are trained to spot instances of potential fraud and to alert customers when this happens but often customers are embarrassed or reluctant to believe they have been scammed.
If you or someone you know believe you have been a victim of these or other financial scams, you should immediately contact your local police department and your bank.
More information about the latest scams can be und on the Federal Trade Commission website.
With the recent uptick in the number and sophistication of financial scams that we are seeing, we want to take this opportunity to remind you to be diligent about protecting your funds and personal information. Check out these six important tips to protect your
funds AND your identity:
- BE WARY WHEN SOMEONE INSTRUCTS YOU TO DOWNLOAD
AN APP ON YOUR PHONE. A new scam has recently been unveiled where scammers create fake apps and trick you into downloading them to gain access to your device and information. Make sure any app you download is legitimate. When in doubt, do some research: visit the app website, check its ratings. Be aware that even legitimate apps can be used fraudulently so be cautious! - NEVER GIVE OUT YOUR ACCOUNT INFORMATION OR SECURITY CREDENTIALS, EVEN IF YOU THINK YOU KNOW WHO IS ASKING FOR IT. We cannot say this enough times! The Bank will never contact you by telephone, text or email requesting you provide personal information such as your account number, debit card number, online banking login information, social security number or personal identification number (PIN). If you call us, however, you will be asked to verify confidential information.
- BE CAUTIOUS ABOUT CLICKING ON LINKS IN TEXTS, EMAILS, POP-UPS OR ADS, ESPECIALLY FROM SOMEONE PRETENDING TO BE YOUR BANK AND LINKS TITLED "URGENT" OR
"WARNING. Scammers will attempt to lure you into clicking on fraudulent links that may allow them access to everything on your computer. - MAKE SURE YOUR DEVICES ARE UP TO DATE. For your financial security, it is important to keep your computers, tablets and phones updated with the latest operating system and security software available.
- REVIEW YOUR ACCOUNTS REGULARLY FOR ANY UNAUTHORIZED OR SUSPICIOUS CHARGES. If you have online banking, it is easy to do! If you do not use online banking, please contact us to set it up.
- PROPERLY DISPOSE OF BANK STATEMENTS AND OTHER PERSONAL INFORMATION. Senior centers and libraries often have shredders and the Bank hosts an annual community shred day every spring.
We want to ensure that you are doing everything you can to protect your funds and personal information. Please call Deposit Services at 978-462-3106 if you have any questions.
- We will never contact you by telephone, text or email requesting that you provide personal information such as your account number, debit card number, Online Banking login information, Social Security Number or Personal Identification Number (PIN). However, if you call us you will be asked to verify confidential information.
- When the Institution for Savings suspects fraud, a transaction alert will be sent via telephone, text, or email; however, we will never ask you to provide confidential information in your response.
- If you receive a telephone call, text or email and have any suspicion, do NOT respond. Instead, contact Deposit Services at 978-462-3106.
- Taking your money or belongings without your knowledge?
- Signing your name without permission?
- Never sign anything you don’t understand.
- Never give away property in exchange for care.
- Know your banker, attorney, or financial advisor.
- Document financial arrangements in writing.
- Check the references and credentials of anyone who wants to work in your home, including utility workers and town employees.
- Beware of door-to-door sales people and telephone sales pitches.
- Don’t give out your bank account number, credit card number, or other personal information over the phone or Internet.
- Stay socially active.
- Never sign anything you don’t understand.
- Plan ahead. Consider a trust or power of attorney.
- Don’t isolate yourself, keep up with friends.
- Get to know your bank personnel.
- Use Direct Deposit.
- Ask for help.
- Report the incident to the card issuer immediately
- Cancel your account and open a new one
- Review billing statements carefully after the incident
- If the statements show unauthorized charges, send a letter to the card issuer via regular mail (keep a copy) describing each questionable charge
- Schedule recurring transfers between accounts
Credit Card Loss or Fraudulent Charges
Your maximum liability under federal law for unauthorized use of your credit card is $50 (policies vary). If the loss involves your credit card number, but not the card itself, you have no liability for unauthorized use; in general, you may only be liable for a very small amount but always check with your individual card company for their exact policy.
- Report the theft to the bank as quickly as possible
- Cancel your account and open a new one
If you have downloaded a virus or 'Trojan Horse'
- Some phishing attacks use viruses and/or a 'Trojan Horse' to install programs called "key loggers" on your computer. These programs capture and distribute any information you type to the phisher, including credit card numbers, usernames and passwords, Social Security Numbers, etc.
- If this occurs, you likely may not be aware.
- To minimize this risk, you should:
- Install and/or update anti-virus and personal firewall software
- Update all virus definitions and run a full scan
- If your system still appears compromised, fix it and then change your password again.
Identity theft occurs when someone uses your personal information such as your name, Social Security number, credit card number or other identifying information, without your permission to commit fraud or other crimes. If you have given this information to a phisher, you should do the following:
- Report the theft to the three major credit reporting agencies, Experian, Equifax and TransUnion Corporation, and do the following:
- Request that they place a fraud alert and a victim's statement in your file
- Request a FREE copy of your credit report to check whether any accounts were opened without your consent
- Request that the agencies remove inquiries and/or fraudulent accounts stemming from the theft
Federal Trade Commission-ID Theft
US Department of Justice
FBI Internet Crime Complaint Center
An Overview for Customers courtesy of Conference of State Bank Services (CSBS)
A fast growing electronic crime where thieves typically use some form of malware to obtain login credentials to Corporate Internet Banking accounts and fraudulently transfer funds from the account(s). Domestic and International Wire Transfers, Business-to-Business ACH payments, Internet Bill Pay and electronic payroll payments have all been used to commit this crime.
- Criminals target victims by scams.
- Victim unknowingly installs software by clicking on a link or visiting an infected Internet site.
- Fraudsters began monitoring the accounts.
- Victim logs on to their Internet Banking.
- Fraudsters collect login credentials.
- Fraudsters wait for the right time and then -- depending on your controls -- they login after hours or if you are utilizing a token they wait until you enter your code and then they hijack
the session and send you a message that Internet Banking is temporarily unavailable.
- Malicious websites (including Social Networking sites)
- P2P Downloads (e.g. LimeWire)
- Ads from popular web sites
- Web-borne infections: According to researchers in the first quarter of 2011, 76% of web resources used to spread malicious programs were found in 5 countries worldwide: United States, Russian Federation, Netherlands, China, & Ukraine.
- Form of malware that deceives or misleads users into paying for the fake or simulated removal of malware.
- Has become a growing and serious security threat in desktop computing.
- Mainly relies on social engineering in order to defeat the security software.
- Most have a Trojan Horse component, which users are misled into installing.
- Browser plug-in (typically toolbar).
- Image, screensaver or ZIP file attached to an e-mail.
- Multimedia codec required to play a video clip.
- Software shared on peer-to-peer networks
- A free online malware scanning service
- What may be relied upon today as an indication that an email is authentic may become unreliable as electronic crimes evolve.
- This is why it is important to stay abreast of changing security trends.
- Some experts feel e-mail is the biggest security threat of all.
- The fastest, most-effective method of spreading malicious code to the largest number of users.
- Also a large source of wasted technology resources
- Examples of corporate e-mail waste:
- Electronic Greeting Cards
- Chain Letters
- Jokes and graphics
- Spam and junk e-mail
- Provide Security Awareness Training for Our Employees & Customers
- Review our Contracts
- Make sure that both parties understand their roles & responsibilities
- Make sure our Customers are Aware of Basic Online Security Standards
- Stay Informed
- Attend webinars/seminars & other user group meetings
- Develop a layered security approach
- Multi-factor Authentication
- Watermark image
- Monitoring of IP Addresses on login
- Challenge questions/phone verification on login and ACH/Wire generation
- User Authority Limits to control account entitlements
- Calendar File – Frequencies and Limits
- Dual Control Processing of files on separate devices –recommended
- Out of Band Confirmation on every wire transfer
- Monitoring of every ACH batch that is originated
- Secure Browser Key
- Secure Token requirement for Cash Management customers
- Education is Key. Train your employees!
- Secure your computer and networks.
- Limit Administrative Rights. Do not allow employees to install any software without receiving prior approval.
- Install and Maintain Spam Filters.
- Verify system users are currently employees and their access privileges align with their job responsibilities.
- Work with IT consultants or dedicated IT staff to implement and maintain Network Segmentation.
- Review and update network security including patch management and access privileges frequently.
- Purchase Cyber Insurance to protect you against Cyber Crime Incidents.
- Surf the Internet carefully.
- Install & maintain real-time anti-virus & anti-spyware desktop firewall & malware detection & removal software. Use these tools regularly to scan your computer. Allow for automatic updates and scheduled scans.
- Install routers and firewalls to prevent unauthorized access to your computer or network. Change the default passwords on all network devices.
- Install security updates to operating systems and all applications as they become available.
- Block Pop-Ups.
- Do not open attachments from e-mail. Be on the alert for suspicious emails
- Do not use public Internet access points.
- Reconcile accounts daily.
- Note any changes in the performance of your computer.
- Dramatic loss of speed, computer locks up, unexpected rebooting, unusual popups, etc.
- Make sure that your employees know how and to whom to report suspicious activity to at your Company and the Bank.
- Contact the Bank if you:
- Suspect a Fraudulent Transaction
- If you are trying to process an Online Wire or ACH Batch & you receive a maintenance page.
- If you receive an email claiming to be from the Bank and it is requesting personal/company information.
- Inability to log into online banking (thieves could be blocking customer access so the customer won’t see the theft until the criminals have control of the money);
- Dramatic loss of computer speed;
- Changes in the way things appear on the screen;
- Computer locks up so the user is unable to perform any functions;
- Unexpected rebooting or restarting of the computer;
- Unexpected request for a one time password (or token) in the middle of an online session;
- Unusual pop-up messages, especially a message in the middle of a session that says the connection to the bank system is not working (system unavailable, down for maintenance, etc.);
- New or unexpected toolbars and/or icons; and
- Inability to shut down or restart the computer.
- The FDIC does not directly contact bank customers (especially related to ACH and Wire transactions, account suspension, or security alerts), nor does the FDIC request bank customers
to install software upgrades. Such messages should be treated as fraudulent and the account holder should permanently delete them and not click on any links. - Messages or inquiries from the Internal Revenue Service, Better Business Bureau, NACHA, and almost any other organization asking the customer to install software, provide account
information or access credentials is probably fraudulent and should be verified before any files are opened, software is installed, or information is provided. - Phone calls and text messages requesting sensitive information are likely fraudulent. If in doubt, account holders should contact the organization at the phone number the customer obtained from a different source (such as the number they have on file, that is on their most recent statement, or that is from the organization’s website). Account holders should not call phone numbers (even with local prefixes) that are listed in the suspicious email or text message.
We encourage you to review the Corporate Account Takeover & Information Security Awareness topic.
- Provide continuous communication and education to employees using online banking systems. Providing enhanced security awareness training will help ensure employees understand the security risks related to their duties;
- Verify system users are currently employees and their access privileges align with their job responsibilities;
- Work with IT consultants or dedicated IT staff to implement and maintain Network Segmentation;
- Review and update network security including patch management and access privileges frequently;
- Update anti-virus and anti-malware programs frequently;
- Update, on a regular basis, all computer software to protect against new security vulnerabilities (patch management practices);
- Communicate to employees that passwords should be strong and should not be stored on the device used to access online banking;
- Adhere to dual control procedures;
- Use separate devices to originate and transmit wire/ACH instructions;
- Transmit wire transfer and ACH instructions via a dedicated and isolated device;
- Practice ongoing account monitoring and reconciliation, especially near the end of the day;
- Purchase Cyber Insurance to protect you against Cyber Crime Incidents;
- Adopt advanced security measures by working with consultants or dedicated IT staff; and
- Utilize resources provided by trade organizations and agencies that specialize in helping small businesses.
- Configuration changes to cash management/online banking profiles:
- New user accounts added;
- New ACH batches or wire templates with new payees;
- Changes to personal information;
- Disabling or changing notifications; and
- Changes to the online account access profile;
- Compromised internal systems used by employees resulting in:
- Inability to log into online banking system (thieves could be blocking the bank’s access while they are making modifications to account settings);
- Dramatic loss of computer speed;
- Changes in the way web pages, graphics, text or icons appear;
- Computer lock up so the user is unable to perform any functions;
- Unexpected rebooting or restarting of computer;
- Unexpected request for a one time password (or token) in the middle of an online session;
- Unusual pop-up messages, such as “try back later” or “system is undergoing maintenance”;
- New or unexpected toolbars and/or icons; and Inability to shut down or restart.
- The FDIC does not directly contact bank customers (especially related to ACH and Wire transactions, account suspension, or security alerts), nor does the FDIC request bank customers to install software upgrades. Such messages should be treated as fraudulent and the account holder should permanently delete them and not click on any links.
- Messages or inquiries from the Internal Revenue Service, Better Business Bureau, NACHA, and almost any other organization asking the customer to install software, provide account information or access credentials is probably fraudulent and should be verified before any files are opened, software is installed, or information is provided.
- Phone calls and text messages requesting sensitive information are likely fraudulent. If in doubt, account holders should contact the organization at the phone number the customer obtained from a different source (such as the number they have on file, that is on their most recent statement, or that is from the organization’s website). Account holders should not call phone numbers (even with local prefixes) that are listed in the suspicious email or text message.
Since each business is unique, customers should write their own incident response plan. A general template would include:
- Contact information for the bank;
- Steps the account holder should consider to limit further unauthorized transactions, such as:
- Changing passwords;
- Disconnecting computers used for Internet banking; and
- Requesting a temporary hold on all other transactions until out-of-band confirmations can be made;
- Information the account holder will provide to assist the bank in recovering their money;
- Contacting their insurance carrier; and
- Working with computer forensic specialists and law enforcement to review appropriate equipment.
Additional Resources for Business Account Holders


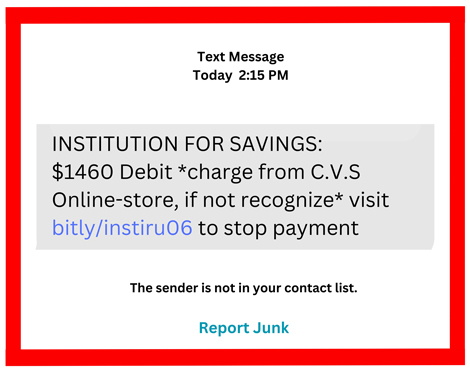 The Institution for Savings does have a fraud department and if it is a legitimate text message or call from us you will simply be asked to confirm activity or tell us if the transaction(s) indicated is fraud. Important: as part of a fraud claim we do not need you to change or provide security credentials or account numbers to proceed. Remember we are the Bank and we have the information we need.
The Institution for Savings does have a fraud department and if it is a legitimate text message or call from us you will simply be asked to confirm activity or tell us if the transaction(s) indicated is fraud. Important: as part of a fraud claim we do not need you to change or provide security credentials or account numbers to proceed. Remember we are the Bank and we have the information we need..png)

